Authentication LDAP
Last modified by Aurelie Bertrand on 2025/12/19 08:51
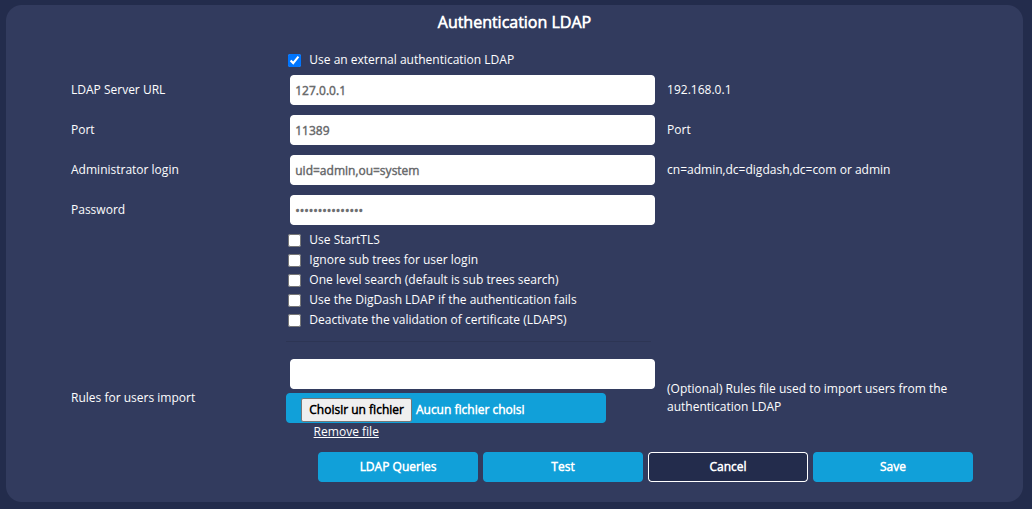
If you want to use an external LDAP for authentication :
- Check Use an external authentication LDAP.
- Enter the parameters for the LDAP server used to authenticate users.
The following options are available:Use StartTLS Use the secure LDAP version on TLS for encrypting the authentication process. Ignore user sub-trees for user login Do not browse subtrees for identification. One level search (default is sub trees search) Do not search all sub-trees. Use the DigDash LDAP if the authentication fails Use DigDash LDAP if authentication fails with external LDAP. Deactivate the validation of certificate (LDAPS) Disable the use of the secure LDAP protocol (LDAP over SSL). - You can load a rules file for importing LDAP authentication users. You can find a commented example of this rules file (ldapmapping.xml) in the documentation/en/sample directory of the DigDash installation.
- Click Validate to accept the changes you have made.
- If you wish to modify the LDAP requests, click on the LDAP Requests link and modify the desired requests.
To import users from this LDAP:
- Open the Configuration -> User Management page.
- In the Authentication LDAP Users section (which is only enabled if you are using an external LDAP server) :
- Type the name of the user you are looking for (or leave the field empty to display all users) and click Search
- Select the users you wish to import and click Import users.
Active Directory LDAP authentication connection
Import users from a domain group
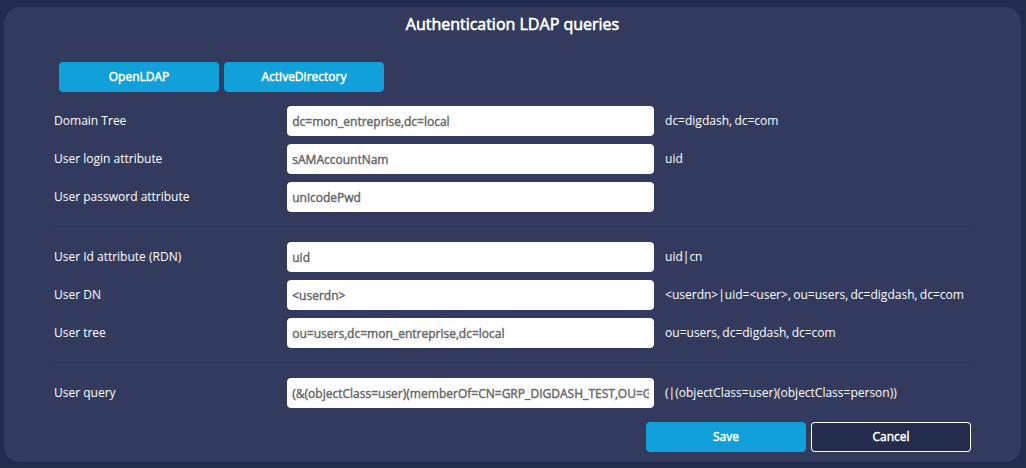
It is possible to refine the LDAP request to filter the import of users affiliated to a single Active Directory domain group. To do this, use the memberOf syntax in the user query.
For example, to import all the users in the CN=GRP_DIGDASH_TEST group in the company_name Active Directory domain, ignoring the other groups, we use the following query:
(&(objectClass=user)(memberOf=CN=GRP_DIGDASH_TEST,OU=Groupes Applis,OU=Groupes de Gestions,DC=nom_entreprise,DC=local))
The DN tree should look like this:
DC=local
└── DC=company_name
└── OR=Management groups
└── OR=Application groups
└── CN=GRP_DIGDASH_TEST
Problems importing users
If you encounter difficulties importing users from an external Active Directory LDAP:
- Check the Ignore user subtrees for identification option.
- In the LDAP request, enter sAMAccountName (or the one that is always filled in) in the User ID attribute (RDN) field.
- Check that the user search on the external LDAP is working.
- Restart the server so that the import works.